Are You Authenticating Application Users?
As we briefly discussed in my last blog, Application Delivery Controllers (ADCs) deploy at the intersection of the network and applications so they can act as sensors to changing user demands – detecting increased user latency, lack of available resources, availability or outage issues. An additional functionality that many of our customers use ADCs for is to authenticate users before letting them connect to applications.
Why Authenticate?
Many application services are web-enabled and sometimes bundled in other composite applications via Application Programming Interfaces (APIs). Since these services are accessible over the web, they are open to malicious attacks.
There are many ways a malicious user can affect an application environment. Social engineering, like impersonating a user identity to access sensitive data, can be used to infiltrate an enterprise. It is also possible to reuse a validated, but hacked user credential to access an application.
As hackers probe network and application vulnerabilities to gain access to sensitive data, the prevention of unauthorized access needs to be multi-pronged as well. To secure data that is in motion and at rest, it is important to prevent Denial-of-Service (DoS) Attacks at the perimeter and prevent rogue application ports/applications from running in the enterprise. Routine vulnerability assessment scans on applications and scanning source code for vulnerabilities can help this.
Authentic vs. Authorized
Another important aspect to preventing malicious access and preventing the breach of sensitive data is to validate users before they can access an application. There are two aspects to this – making sure that the user is “authentic” and that they are “authorized” to access the application.
 To prove user authenticity, the identity/credential must be validated against an identity store (LDAP, Active Directory, etc.). If seen for the first time or based on risk criteria, the user may also be challenged for additional factors – say to provide a passcode or a one-time password. It’s also important to make sure that the tokens that are generated after validation, sometimes used for single sign-on (SSO) are also secure.
To prove user authenticity, the identity/credential must be validated against an identity store (LDAP, Active Directory, etc.). If seen for the first time or based on risk criteria, the user may also be challenged for additional factors – say to provide a passcode or a one-time password. It’s also important to make sure that the tokens that are generated after validation, sometimes used for single sign-on (SSO) are also secure.
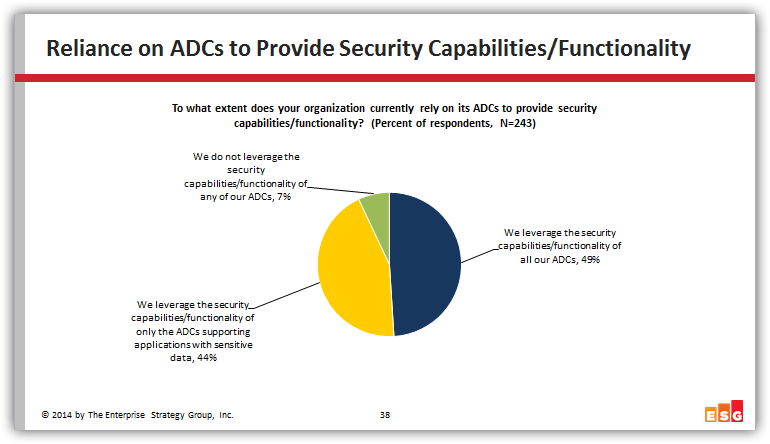
Since ADCs are generally used to terminate user connections, data should be scrubbed to discover malicious application attacks prior to connecting user to an application. This method of authenticating users against an identity management system prior to accessing applications is one of the functionality that many of our customers routinely offload to ADCs.
In addition to validating access, sometimes applications also have to authorize access. Is this user allowed to access a particular application or functionality – say for important financial data, or patient information? Many legacy applications are built with authorization code coded.
Even if your applications are deployed and working as designed, apply rigor to securing them to prevent breaches. Your practice should include DDoS prevention and mitigation, unauthorized ports and applications, encrypting data at rest and in motion, access and authorization enforcement, auditing and logging.
Click here to Learn More about the Expanding Role and Importance of Application Delivery Controllers



