Data on Demand: From Smartphones to Tablets, How Mobile Carriers Can Optimize Mobile Services
Mobility is without a doubt, a big part of the IT landscape. As employees increasingly use enterprise applications (such as CRM, ERP and HR applications) while on the go, the enterprise workforce has become more mobile. Adding to this, employees utilize their own mobiles devices for application access (BYOD – “bring your own device”), which means an increase in the variety of mobile devices from both compatibility and security viewpoints. Even outside of the enterprise, many of us increasingly use iPhones, iPads or Android-powered mobile devices for reading emails, chatting, streaming videos, browsing the Internet and more. I recently came across an interesting chart that explains it all:

It clearly shows that the number of mobile-only users is expected to increase from 14M to 788M in a period of just 5 years!
The increase in the number of mobile-only users does not only mean more traffic and more capacity to be handled – which is something that mobile carriers definitely have to cope with. But there’s something else here that’s of concern. Performance-wise, mobile users are more prone to latency issues. Lower bandwidth, higher latency, smaller memories and lower processing power associated with mobile devices and networks lead to slower repose time.
Mobile carriers strive to provide the best user experience compared to their competition, otherwise they risk increasing their churn rate. So what can mobile carriers do to optimize their services? Here are a couple of recommendations.
-
Use high-capacity application delivery controllers (ADC). For tier-1 and tier-2 carriers, the total throughput of mobile traffic became a two-digit number (i.e. >10Gbps) a long time ago. Hence, it’s recommended that such carriers deploy high-end ADCs that can address up to 80Gbps, maybe more, of throughput capacity – and one that can preferably scale over time as mobile services expand.
-
Have a high-performing ADC. It’s mandatory that the ADC is able to process high throughput, but this is definitely not enough. When also taking into consideration the mobile quality of experience, it’s important that the ADC also delivers good performance, in terms of layer 4, layer 7 and SSL (in case the service is secured). Otherwise, throughput may be fine, but the number of connections / requests would be the actual bottleneck.
-
Implement next-gen connectivity. Make sure the ADC you deploy is equipped with 40GE ports, the new standard in data center switching. This will ensure that the large amount of traffic can be effectively pushed from the switches to the server via the ADC, and vice versa.
-
Allow for multi-flow capabilities. Many times, a mobile transaction traverses a complex route inside the carrier data center. For example, it might start from the S-Gateway, go to the core switches, then go to the ADC, then go to some VAS (e.g. spam filtering), then to another VAS (e.g. parental control), then to a third one, etc. – and only then be actually sent to the server. Hence, it’s vital to have an ADC that can intelligently route the mobile transaction per context/attributes/session to the various VAS, eliminating transaction overhead.
-
Integrate policy enforcement functions. Mobile transactions need to be authenticated and authorized before they do what it they’re supposed to do. For that reason, it’s critical that the ADC is integrated with PCRF, AAA protocols (such as Diameter, RADIUS, etc.) and other policy enforcement functions in the mobile core network. This will simplify the mobile service design and allow for a more agile mobile service delivery (e.g. policy changes can be done from a remote, centralized console).
-
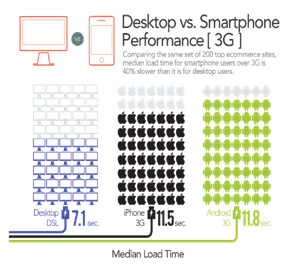
Accelerate. “Each round trip can take 20-50 milliseconds for desktop browsers – and up to a full second each for mobile users” – taken from Radware’s State of the Union Report, Spring 2013. By using best-in-class web performance optimization (WPO) techniques that leverage both the server end and the end-user devices, mobile transaction response time can be reduced – resulting in better quality of experience. Such service can be also used via a cloud service, eliminating the need to integrate and deploy it into the carrier data center. To add additional data to the last recommendation, here’s another interesting chart:

It simply shows that from a quality of experience perspective, the median load time of iPhone and Android devices is ~60% slower compared to a desktop. It’s something to ponder, especially when projections show that mobile devices are soon going to be used by the majority of Internet users.
-
Monitor. You can’t manage what you can’t measure. Using a monitoring service one can gain visibility into transaction SLA and its completion. It enables you to instantly see what’s wrong in the network/application before you start to get the “angry calls” from your users. Therefore, a monitoring service is a very important component, which will direct you to which actions should be taken to remedy application or network issues.