ERT ALERT: Cyber-attack Against U.S. Based Websites on May 7th – 4 Attack Methods to Expect
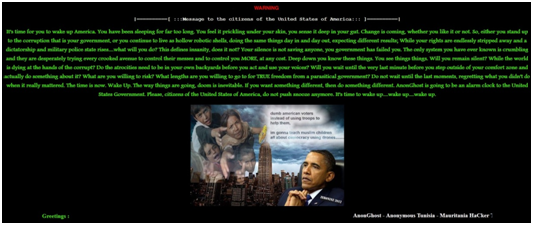
AnonGhost – A hacking group affiliated with Anonymous announced a new cyber-attack campaign against US websites named #OPUSA. The attack is scheduled for May 7th, 2013.
This attack campaign follows a recent and similar attack campaign organized by AnonGhost that took place exactly one month earlier – on Apr 7th, 2013 and was launched against Israeli web sites (aka OPISRAEL).
Similar to the Israeli web site attacks, numerous Anonymous and several other cyber hacking groups have announced their participation in the upcoming attack campaign. The most noteworthy, although not yet confirmed, is the Izz ad-Din al-Qassam cyber fighters which are believed to be responsible for the recent attacks on American banks and financial institutions.
Several U.S. based web sites have already been defaced. The content injected into the hacked sites is used to promote the upcoming attack campaign.
What to expect?
At this time, no public announcements have been made regarding specific attack methods or attack tools that would be used during #OPUSA. However, we assume similar attack patterns deployed during #OPSISRAEL may be used again in this upcoming cyber attack due to the close relationship of both attack campaigns.
These methods include:
- Using common vulnerabilities to perform web site defacement and private information leakage from backend data sources.
- Bandwidth saturation attacks using common Distributed Denial-Of-Service attack tools such as Mobile LOIC, LOIC and HOIC.
- Consumption of web server resources using “Low and Slow” attack tools such as Slowloris, Pyloris, R.U.D.Y – note that these attacks were shown to be using HTTPS as well as HTTP protocols.
- If groups similar to Izz ad-Din al-Qassam cyber fighters join the attack campaign, we may also expect distributed attacks originating from dedicated attacking servers. These attacks could cause huge traffic peaks and will be harvesting the power of server based botnets such as Brobot (aka Itsoknoproblembro).
Radware’s ERT will continue to monitor information around the May 7th #OpUSA attack and will provide updates as frequently as possible in order to keep you informed and prepared.
