How to Evaluate a Vendor for DDoS & Cyber-Attack Protection
In my last blog we discussed if low cost “always-on” DDoS protection can keep you safe. We started to outline the key requirements for a DDoS vendor and now I’d like to continue this point.
How Can An Organization Protect All Enterprise Assets—No Matter Where They Reside?
In many organizations, data centers operate in multiple locations while a growing portion of the infrastructure lives in the cloud. Dispersing the IT infrastructure introduces as many challenges as benefits. With the safe borders of the perimeter no longer protecting all enterprise assets, existing security measures need to be re-evaluated.
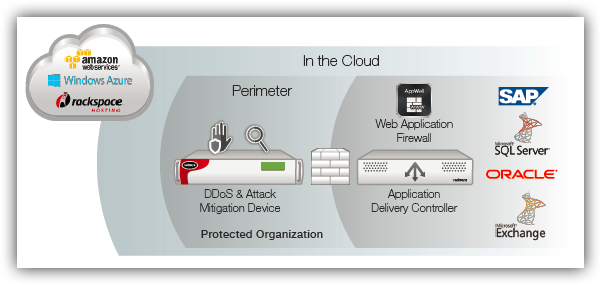
While enterprise security is evolving, so are cybercriminals and attacks. It has become common knowledge that there is no way to prevent attacks – but there is a very strong need to mitigate them. If an organization’s DDoS security strategy does not take that into consideration, the organization and its users are at risk.
What is the key factor for a successful security strategy? One that truly benefits from all the advantages of the advanced detection and DDoS mitigation solutions deployed in the organization? The answer seems to be a shift from location to communication. As the locations of detection and mitigation tools continually increase, the need for a coordinating mechanism – both human and machine based – grows, as well.
Distributing the detection and mitigation layers across all enterprise application infrastructures can deliver a global view of network behavior and the attack states. Information collected from all detection tools needs to be correlated and analyzed to determine which mitigation process to use.
Now, what are the key criteria for detection and mitigation when evaluating a vendor for DDoS and cyber-attack protection?
Assess each vendor for these criteria – aiming to maximize capabilities in each area:
How Good Is The Vendor At DETECTION?
Quality
This section evaluates the ability for the vendor to provide high-quality detection:

Type(s) of Detection Available
- Netflow
- Packet L7 Headerless
- Openflow
- Coverage of OWASP Vulnerabilities
- Packet L3/4
- Inputs/Signals from Other Mitigation Tools
- Packet L7 Header Required
- Deployment Model Options
- In-Line
- Cloud Scrubbing Center – Asynschronous
- OOP – Synchronous
- Software Defined Networking (SDN)
- Hybrid Cloud Options
- Virtual Deployment Options
- Internal Scrubbing Center – Asynschronous
- Feeds from Partners/Works with Other Vendor Signals
Time
This section evaluates the categories required for modern attack detection:
- Real-Time Options
- Signaling/Automatic Options (for Advanced Application Attacks)
- Signaling/Automatic Options (for Cloud Diversion)
Reporting & Response
This section evaluates the categories required for controlling and reporting modern attack detection:
- Real-Time
- Detection Support Response – Real Time
- Historical
- Detection Support Response – On-Site Options
- Forensics
- Integrated Reporting with Cloud Portal
- Intelligence Reporting
- Ability to Discern Legitimate vs. (that is, can detect before an attack) Illegitimate Traffic in Real-Time
How Good Is The Vendor At MITIGATION?
Quality
Does the vendor over-mitigate or under-mitigate the threats? How many technologies are leveraged to assist?
- Rate-Only
- HTTP Server-Based Protections
- Routing Techniques
- HTTP OWASP-Based Protections
- Rate Behavior Only
- Hybrid Signaling/Cloud Scrubbing Center Coordination
- Other Than Rate Behavior
- SSL Protections
- Heuristic Behavior
- HTTP Redirects
- Statistical Behavior
- JavaScript Challenge & Response
- Signatures – Static with Update Service
- Cloud Challenge Response
- Signatures – Custom Real Time
Time
How quickly can the vendor begin mitigation?
- Real-Time Options
- Automatic Options
Reporting & Response
How granular is the reporting? Can a user see if legitimate traffic is being impeded by the mitigation technique?
- Real-Time Displays
- Displays All Attacking Vectors Granularly
- Historical Mitigation Effectiveness Measures
- Mitigation Response Attack-Back Options
- Forensics & Detail Reports
- Mitigation Support Response – Real Time
- Emergency Response Options
- Mitigation Support Response – On-Site Options
- Displays Legitimate & Illegitimate Traffic
- Integrated Reporting with Cloud Portal
For The Full Evaluation Check List, Download Your Copy Of The DDoS Handbook.
