Cybersecurity in the Real World: 4 Examples of the Rise of Public Transportation Systems Threats
Public Transportation is the lifeblood of any economy and the circulatory system of modern day societies. From train, plane to automobile, the public transportation apparat is one of the core achievements in a highly functioning society. It includes everything from the roads, shipping ports and airports which are funded and maintained by public investments to wholly run publicly available train and bus systems.
Many people realize that modern day conveniences are fleeting and assumptions are made every day about things we need to make a living. The availability and sanctity of a modern day public transit is one of those assumptions. So given this, how safe is public transport from cyberattacks and is there evidence that this system could be crippled by hackers up to no good?
There is strong evidence that the public transportation system needs dramatic investments in order to stay safe and sound from cyberattacks and the following three examples serve as real-life examples of what already exists and has occurred:
3 Examples: Cyberattacks / DDoS Threats to Air Transport Industry
In order to keep the global aviation system operating smoothly, the industry relies on information and communications technology (ICT) to deliver critical information, empowering the people working within the network. It is clear that airport infrastructure supports many different operations that are critical for the efficiency and effectiveness of the air transport system and availability of these systems is paramount.
The following graphic from helps illustrate the many risks to the Air Transport Industry:
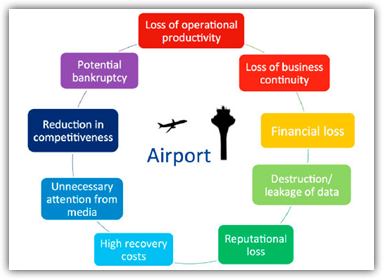
Cyber-security incidents are dramatically increasing year-over-year across the full spectrum of international trade. Due to their visibility, disruption of the essential operations of airlines and airports could feasibly be the subject of a cyber-attack by cyber terrorists
For example, according to the Norwegian publication Aldrimer.no, a cyberattack launched by a Russian APT group may have jammed Sweden’s air traffic control capabilities in November 2015.
Even as the aviation agency’s representatives were busy detailing to media outlets the solar storm that they claimed “created disturbances in the Earth’s magnetic field, which affected radar installations” (despite no nearby countries experiencing a disruption), Swedish officials were alerting NATO that the agency was being targeted in a serious cyberattack, according to the publication.
In June 2015, one of Poland’s airlines, LOT, suggested that its operations at its Warsaw Chopin Airport hub were disrupted by what the carrier said was a cyberattack on its flight planning computers. Ten flights were canceled and other delayed. The problem was widely reported to have been most likely caused by what is known as a Distributed Denial of Service (DDoS) attack — when a hacker deluges an organization’s system with so many communication requests that it overloads the server, and it can no longer carry out its normal functions.
"This was a capacity attack, which overloaded our network," said the LOT spokesman, Adrian Kubicki.
Another such example would be the attack on Istanbul Atatürk and Sabiha Gökçen airports a few years prior to the Polish attack. In July 2013 the passport control systems at the departure terminals in both of these airports were shutdown by a cyber-attack. Passengers were forced to stand in line for hours, and the majority of flights were delayed. Even though the systems were restored, the damage could be felt for many hours after. Unfortunately, not all airports have implemented cyber-security systems that would protect and control those operations and all related features. It simply means that even though many may have security measures in place, cyber criminals, ‘hacktivists’, or cyber terrorists may consider this as a perfect opportunity to attack the airports in many different ways.
This week I participated in a fascinating discussion on threats to Aviation at Embry-Riddle Aeronautical University where we discussed many aspects of this issue on camera. In a previous blog articles, I’ve talked specifically about whether or nota Boeing 777 airliner can be brought down by a cyber attack. . And my colleague recently talked about the impact of last year’s Volkswagen hack to IoT security.
Example Four: Cyberattacks against Seaports and Maritime Operations
In 2013, the BBC reported that Police in Belgium publicly disclosed an attack on the Antwerp Shipping port which had been purported to have taken place over a two-year period from June 2011.

Prosecutors say a Dutch-based trafficking group hid cocaine and heroin among legitimate cargoes, including timber and bananas shipped in containers from South America. The organized crime group allegedly used hackers based in Belgium to infiltrate computer networks in at least two companies operating in the port of Antwerp. The breach allowed hackers to access secure data giving them the location and security details of containers, meaning the traffickers could send in lorry drivers to steal the cargo before the legitimate owner arrived.
Workers were first alerted to the plot when entire containers began to disappear from the port without explanation.
Six months ago in October, 2015, the potential risk of cyberattacks on U.S. ports was raised by the Rep. Candice Miller, R-Mich. Miller. At that time she said, “As a result of asserted security gaps left unfixed by the Department of Homeland Security, a cyberattack against an American port could have dangerous consequences.”
[You might also like: 4 Reasons Future Cyber-Attacks Could Be Terrorizing]
The potential risk was also spotlighted by the Government Accountability Office’s information security issues director, Gregory C. Wilshusen, who stressed the importance of halting cyber-attacks and security breaches at ports.
Miller said: “The Coast Guard, and DHS as a whole, have been slow to fully engage on cyber security efforts at the nation’s 360 seaports…The Coast Guard has not yet conducted cyber risk assessments, though some individual ports have taken the initiative themselves.”
The potential risk was also spotlighted by the Government Accountability Office’s information security issues director, Gregory C. Wilshusen, who stressed the importance of halting cyber attacks and security breaches at ports
Conclusions: How to Solve the Problem?
In the end the threats to public transport are serious, real and numerous. Although I chose to leverage some boutique attack examples which were widely publicized, there are scores of harder hitting examples from traffic lights, to trains, to automobiles.
The key to understanding the solution is to understand that the threat is immeasurably more serious to this industry then many others which are only really concerned with business continuity and financial losses. In this industry we must concern ourselves with the great possibility of loss of life scenarios.
In general, information security people have long understood these risks, but the transportation and manufacturing industries are just now waking from their mental slumber. The key to solving these problems is first to accelerate the awareness of the real possibilities of these dangers, then to assemble a well-orchestrate cybersecurity risk and mitigation strategy for each attribute of public transportation whereby we rely on automation where human life can be placed in harms way.

