Darknet 101: An Introduction to The Darkest Places Online
In my last blog, I talked a little about the general principles of the cyberattack marketplace. Today, we will take a closer look at the Darknet. There is so much talk these days about the Darknet. It’s the stuff of crime novels – a hotbed of criminal activity where anything can be bought and sold.
While that is true, the Darknet also provides an anonymizing layer to journalists and activists around the world who fight for the freedom of information and privacy. It is often a place where they can securely and anonymously communicate with their contacts.
But first, what exactly is the Darknet?
- Darknet – A Darknet is an overlay network that can only be accessed with specific software, configurations, or authorization, often using non-standard communications protocols and ports.
- Dark web – The Dark web is content that exists on Darknet, overlay networks which use the public Internet but which require specific software, configurations or authorization to access.
- Deep web – The Deep web is parts of the World Wide Web whose contents are not indexed by standard search engines for any reason.
- Clearnet – The Clearnet is a term typically referring to the unencrypted, or non-darknet. This traditional world wide web has relatively low-base anonymity, with most websites routinely identifying users by their IP address.
To be clear, the Darknet is a dangerous place where illicit or underground activities are conducted and can be found if you look for them. One of the most predominant features found on the Darknet are the digital marketplaces where different types of goods and digital items are bought and sold mainly for bitcoin and other cryptocurrencies. Today we see a number of growing marketplaces found on both the Clearnet and the Darknet. These sites sell almost anything you can think of and are often a one stop shop for would be criminals.
Items found in the marketplace include:
- Software/Malware
- Security/Hosting
- Counterfeit
- Drugs
- Guns
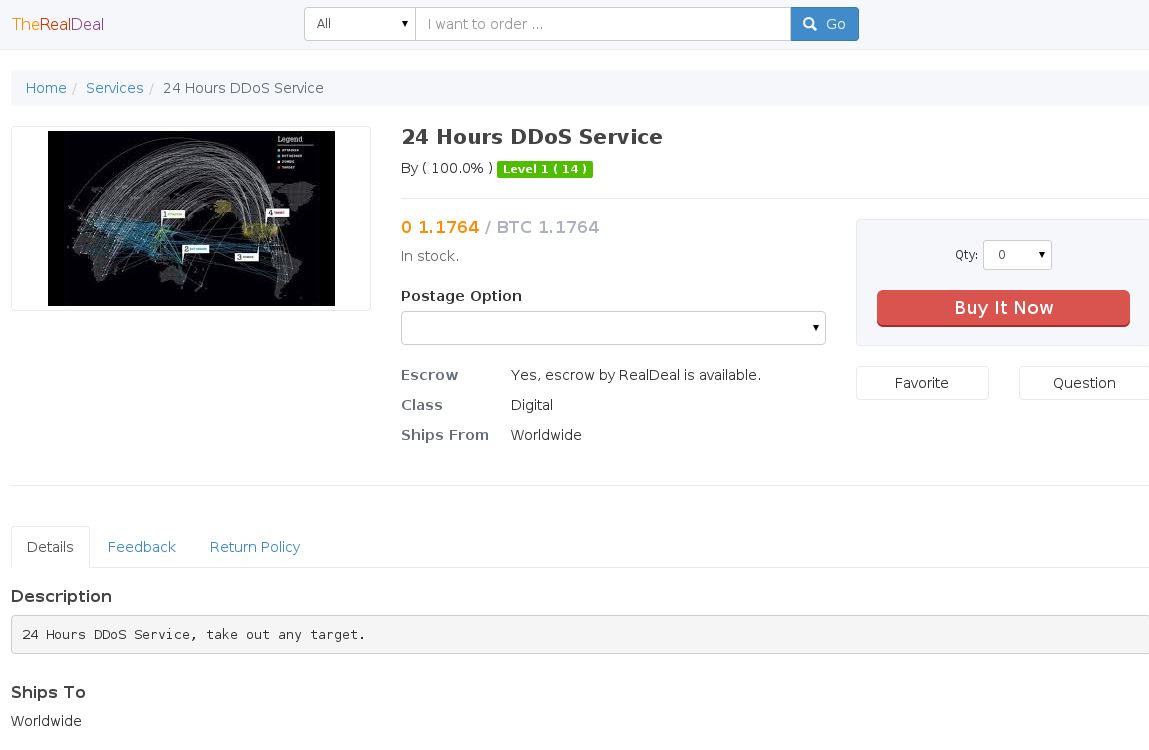
Figure: 24 Hour DDoS service
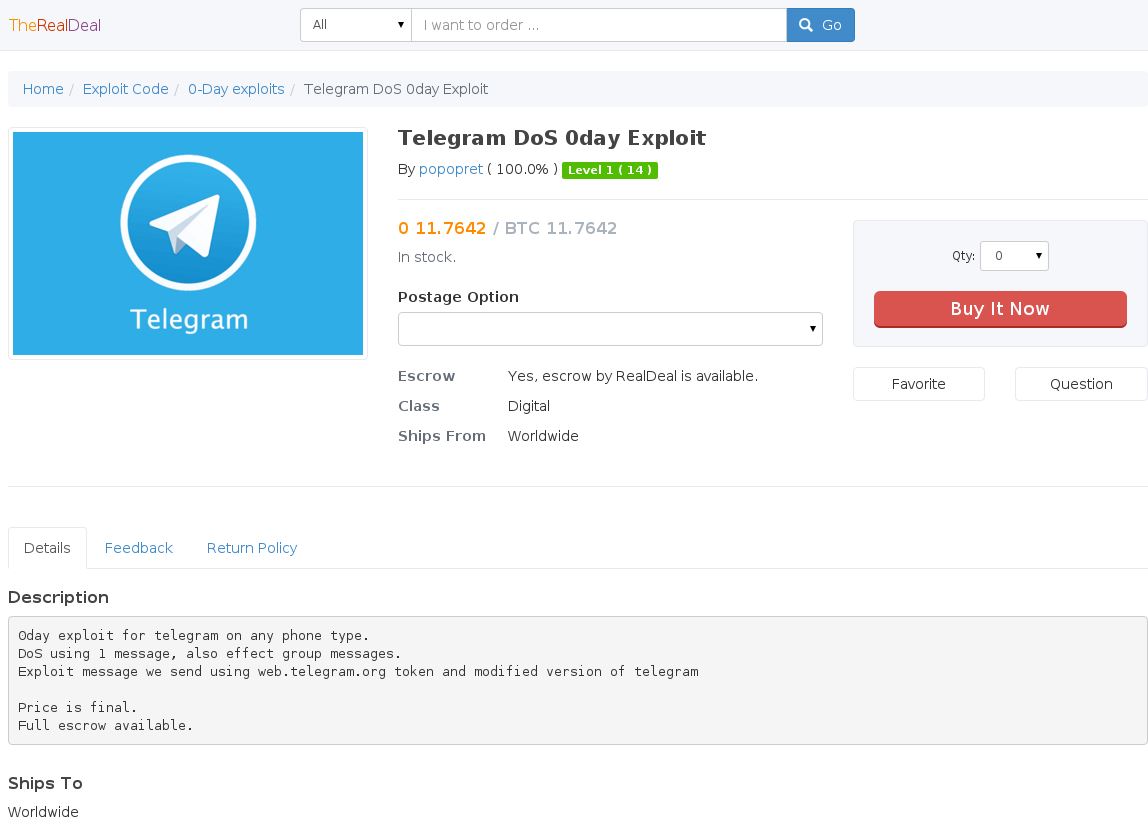
Figure: DoS 0-day exploit for Telegram
[You might also like: Cyber Attack Market Place]
How do I get there from here?
People often think that accessing the Darknet is a technical and complicated task. In reality accessing the Darknet has become very user friendly over the last several years. Both I2P and Tor offer great documentation for novice users and there are plenty on forums and tutorials out there to help educate those that want to learn more about the networks. The only part of the Darknet that actually requires a membership or invitation to join are certain marketplaces that want to control who can see and access the services that they are offering.
When accessing the Darknet you have many options to choose from. Two options include Tor, The Onion Router, and I2P, the Invisible Internet Project. Each has their own advantage and disadvantages and selection for use should be based on the user’s intentions.
Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in encrypted layers and sends them through a bi-directional circuit of relays through the Tor network. Tor also provides a central directory to manage the view of the network.
The Tor Project offers entry-level documentation for its new users and is easy to use. Tor over the years has become very popular with the common user. The Tor Browser Bundle made connecting to Tor very simple for the average user. Tor has received a large amount of academic review over the years and is a very well-funded project. One issue that still remains with Tor is the trust of exit nodes. Attackers can set up malicious exit nodes or spy on the traffic coming out of the network. The best use for Tor is for anonymous out proxing to the internet.
I2p is an anonymous peer-to-peer network overlay that focuses on internal services. It allows users to send data between computers running I2P with end-to-end encryption. I2P uses unidirectional tunnels and layered encryption versus Tor bi-directional tunnels.
I2P is not a very well-known service in comparison to Tor. It has received limited academic review but contains great documentation for all of its users. One issue regarding I2P is the limited number of out proxies to the internet. The best use for i2P is for peer-to-peer file sharing.
Accessing some of these market places on the Darknet can be a challenge if you do not know what you are looking for. Many times you can find lists of hidden services or .onion links on Clearnet sites like Reddit and DeepDotWeb. TheHiddenWiki.org is also a great place to start looking for hidden services and marketplaces along with DNstats.net. DNstats provides updated information about the current status of certain marketplaces along with news about new sites as they become available.
Darknet Marketplaces Include:
- AlphaBay
- Valhalla
- Dream
- Hansa
- The Real Deal
- DHL
- Outlaw
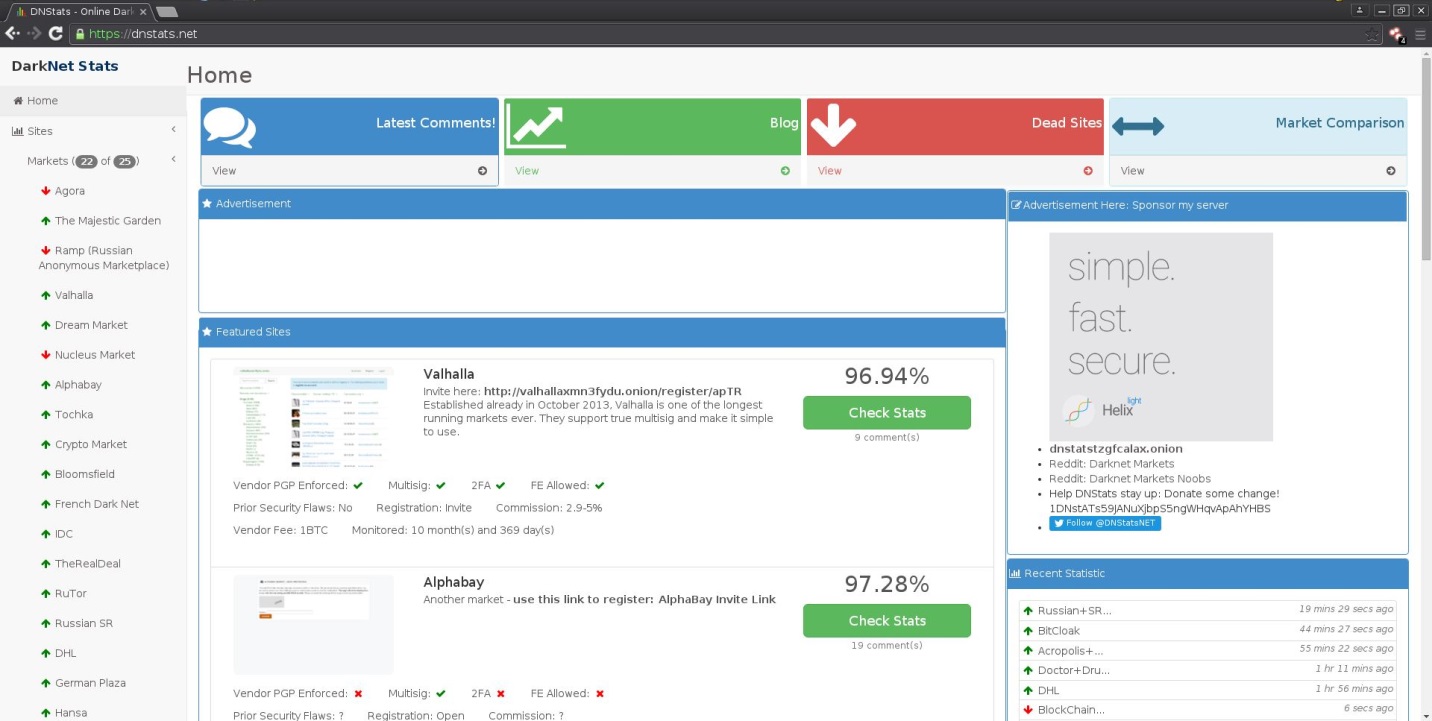
Figure: DNstats, a Darknet status page
[You might also like: 5 Ways Hackers Market Their Services]
There are also a few search engines to help you find what you are looking for on the Darknet. Two popular Darknet search engines are Grams, http://grams7enufi7jmdl.onion/, a Google looking knockoff and Torch, http://xmh57jrzrnw6insl.onion/. Both of these sites will allow you to search for content in the marketplaces and other hidden services found on the Darknet.
Exploring the Dark Markets:
These markets are not exactly special or unique but they have grown in popularity following the Silk Roads take down. Some markets can also be found on both the Darknet and the Clearnet. Sites like 0day today, hack forums, TorCrds, Hell and others sell similar items found on the Darknet and they almost always deal in bitcoin as well. You can also normally find some of the same services available on the Darknet on a number of hacker forums as well.
Hacker Forums
- V3rmillion
- Raid Forums
- GreySec
- RealForums
- Evilzone
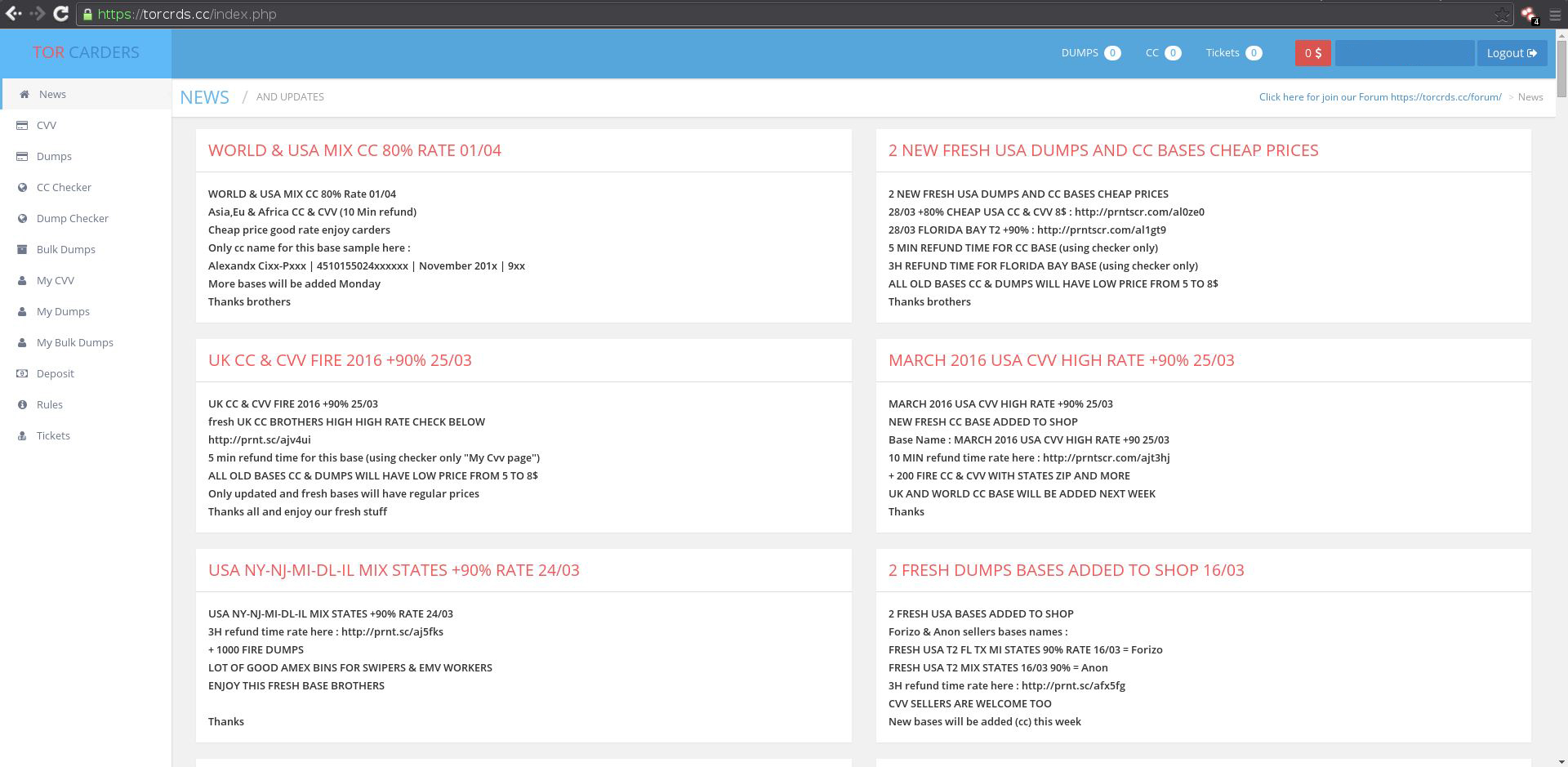
Figure: Torcrds.cc, a website selling stolen credit cards on the Clearnet
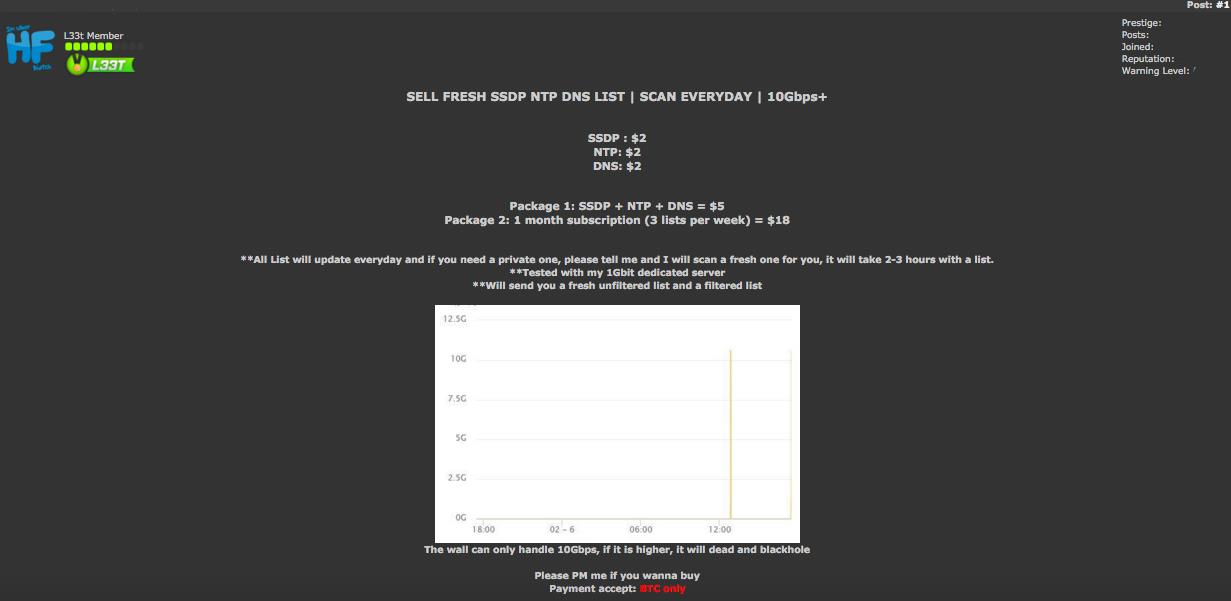
Figure: HackForums users selling SSDP NTP and DNS list for amplified attacks
Most vendors usually deal in Bitcoin or other types of cryptocurrencies. On many of the sites the vendors have to pay some form of a bond to be allowed to sell items or services on the site. These bonds can cost anywhere between .1 to 1 BTC. Some of these sites are also closed to the public and require a referral to join the marketplace.
Some of the newest marketplaces this year include LEO Market, TheDetoxMarket and Apple Market. Last year there were around a dozen new sites that popped up. Some of these sites do not last long on the Darknet as they are often hacked or taken offline by their competition. The growth of the attack marketplace and the utilization of an anonymizing network like the Darknet will continue to grow over the next several years as the entry level for hackers keeps lowering.
In the next blog I will be talking about what an attacker can purchase on the underground marketplaces and what the going rate is for things like DDoS, Ransomware and more. We will be looking at some of the tools and services that are available for potential attackers along with how transactions work in the marketplace.

