Sustained Vigilance Key for Financial Services Organizations in Light of Stable, Steady Threat Landscape
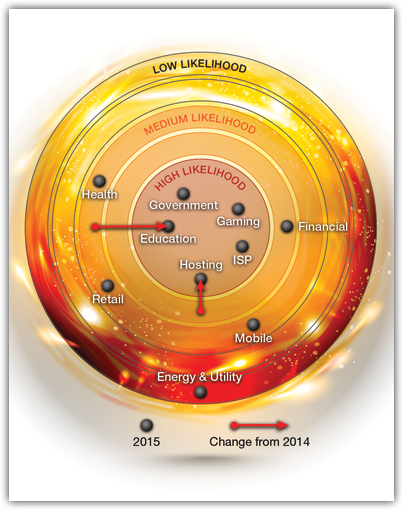
Every year when we publish our Global Application & Network Security Report, one of the most popular aspects of the report is what we call our “Ring of Fire.”
The Ring of Fire presents a graphical representation of evolving and relative risk from cyber security threats across some of the most commonly targeted industries.
The plotting of industries in the ring is a typical combination of art-and-science, combining the quantitative inputs of direct user response via survey, data about the frequency of attacks we’ve seen defending many organizations across these industries, and also a healthy dose of qualitative input from our Emergency Response Team (ERT) on sophistication of attacks as well as general trending on things such as the undercurrents of chatter within the threat community.
As the first in a series of blogs looking specifically at one industry, this blog will dive into the trends ongoing within the Financial Services arena.
Stable, but Still a Key Target
It will come as a surprise to none that the Financial Services industry remains one of the most active from a cyber-security threat and action standpoint. In the case of the 2015 Ring of Fire, we have plotted this industry in the same ‘ring’ as last year, specifically in the “medium likelihood” ring. In our 2014 report, the Financial Services industry was an outlier in that it moved outward, from the “high likelihood” center out to the medium ring.

It’s important not to misinterpret what this means… in 2012-2013, Operation Ababil created a new and extremely high ‘watermark’ for the industry in terms of frequency and intensity of cyber-security attacks. In response to these attacks, most tier 1/2 financial service providers implemented a number of new or updated security capabilities. The movement out from the center ring in last year’s report was primarily a reflection of the attack volume coming down off of Ababil and the improved security posture resulting from new security investments.
This year’s report suggests that the Financial Services space has been stabilized to some degree, though vigilance in maintaining strong security posture against an ever-evolving threat landscape remains paramount. All over the world, attacks on these institutions continue. Typically, these groups demand Bitcoin or another form of crypto-currency to stop the attack, as in the recent ransom-based DDoS attacks on Greek banks. 2015 brought an increase in both the average ransom amount and the number of groups attacking financial targets.
Financial services are also targeted to gain access to information they hold. Information gained through data breaches in banks and corporations can be used through extortion for financial gain. In December 2015, hackers leaked customer data after a United Arab Emirates Bank failed to pay the $3 million ransom the hackers demanded. In addition, the stolen information is often sold in black markets, leaving the banks with the task of managing the crisis of customer data retrieval and fraudulent transactions.
[You might also like: Early Attack Activity Forcing New Thinking in Healthcare IT/Security]
Listening to what the industry is telling us
Information security professionals from the Financial Services space are always among the most active participants in our quantitative study on cyber-security threats, and this trend continued with this year’s report. About 15% of total responses came from Financial Services organizations, representing the second largest single industry in response (trailing only telecommunications providers).
In conducting a review of responses specifically from this industry, a few interesting and notable trends emerge related to what kinds of threats they are facing today, how they are responding to threats, how they regard impacts from those threats, and also where they see the threat landscape going.
In many areas, Financial Services organizations mirror their counterparts in other industries on common and ongoing threats. There are modest increases with regard to the frequency of the top 3 threats (DDoS attack, Phishing, online fraud), with each representing about a 20-30% lift over others, but the stack ranking of threats is pretty consistent across all industries.
One area the financial services area stood out significantly from others is with regard to the frequency of advanced application threats, for instance the threats that make up the Open Web Application Security Project (OWASP) Top 10. These include attacks such as SQL injection, cross site scripting, and cross site request forgery. 98% of respondents in the Financial Services space reported incidence of these attacks versus 90% for other industries. What’s most notable about this is it is an indication that attackers are looking to exploit the trend within the commercial banking space to increase online engagement levels with customers, exposing new points of vulnerability and expanding their attack surface.
Not surprisingly, Financial Services organizations also report a higher rate of SSL or encrypted attacks than others. 44% of respondents from Financial Services say they have been hit with an attack seeking to evade detection by sending through encrypted malicious traffic. We fully anticipate that this trend will continue. Financial Services providers naturally are expected to support encryption around sensitive financial transactions, and adversaries know this. They also know that relatively few security solutions do a good job of inspecting encrypted traffic to be potentially unwanted, malicious traffic.
Speaking of the shortcomings of certain security products, another area where Financial Services organizations differ from other industries is the frequency with which they see firewalls becoming the failure point during attack. Specifically, 39% of respondents from finance (versus 23% on average) claim that firewalls have gotten knocked offline, often the result of a DDoS attack that fills the session tables. For the financial services space, this represents the number one failure point whereas for others, Internet pipe saturation was the top failure point during attack. This also speaks to sophistication of the attacks often targeting financial service providers.
Some Variance in Security Tools
By in large, the Financial Services industry is using a lot of the same security products and services as other industries. There are a few exceptions or areas where their use differs, however.
Financial services organizations are about 40% more likely to be currently using some form of on-premises equipment (70% versus 50%). This is a reflection of the importance the industry puts on managing certain assets within their own data centers whereas other industries may be more aggressively moving assets into cloud hosting environments.
The industry is also more likely to be active users of dedicated DDoS attack protection. Fully, 87% of respondents from the Financial Services space indicated that they already are using or plan to implement DDoS protection, versus 67% of the total respondent pool.
Likely as a result of the aforementioned frequency of OWASP Top 10 style application attacks, Financial Services organizations are also consuming application security components at a higher rate than others, with the most commonly used tools or services including penetration testing, on-premises Web Application Firewalls, and Static Application Security Testing (SAST).
[You might also like: Securing Online Assets: Four Steps to Protect Your Online Business]
What’s Keeping Financial Services Up at Night?
When we explore the general impressions of where attacks come from, where the trends are leading, the Financial Services industry has some inputs that vary from others.
In general, the industry is anticipating attack frequency to maintain a steady state. Respondents from other industries were twice as likely to say they anticipate a 50% increase in attacks (8% versus 4%). However, that steady state already represents a greater frequency than others, as 37% of respondents from Financial Services organizations anticipate daily or weekly attacks versus 27% of the total respondent pool.
For me, one of the most interesting aspects of looking at the inputs from Financial Services organizations relative to others is around their perceptions around motive of attackers. More so than any other industry, the Financial Services industry believes the source of attacks comes from professional hacking (or attacking) organizations primarily motivated by financial gain. Makes sense, right? Attackers are after the very financial assets they hold and protect. However, Financial Services professionals feel somewhat less at risk of attack from hactivist groups than others (13% feel at risk). Yet, we know hactivism has been a key motive behind many attacks on banks. As symbols of wealth and sometimes capitalism, financial institutions are frequently the target of hacktivist campaigns. In fact, there is a very recent example through Operation Icarus, which was a series of offline and online actions coordinated by Anonymous intended to bring to public attention what they see as widespread corruption within the industry and situations of supporting or even funding “global terrorism.” Just goes to show that in all likelihood, someone somewhere has an issue with what your organization is doing, and hactivism can never be ruled out as a motive behind attack. You can read more about OpIcarus here.
Overall, the inputs from the Financial Services space reflect a great deal of common thinking and observations about the threat landscape across industry. We can see business-driven trends around increased consumer engagement creating new points of vulnerability that are forcing new security focus. As we progress through 2016, it will be interesting to see if broader IT trends such as cloud migration and DevOps start to creep more deeply into Financial Services environments and affect results as we work towards next year’s report.

