Ransomware Takes Center Stage As A Major Corporate Cyber Security Risk
It’s 9:30am. You’ve gotten your morning coffee, checked your email, and now you are surfing the web when all of a sudden everything freezes. A message pops up on your screen saying:
“You have been caught accessing inappropriate content and your device will remain locked unless you pay $$$$$”
Ransomware is fast becoming the leading cyber concern for businesses in 2016. We are seeing new ransom tactics used daily to target companies from various industries and individuals worldwide. The potential harm is devastating. We saw recent attacks in Switzerland, Germany, Lithuania and Israel, as well as several attacks against hospitals across the US and Canada.
Unlike other types of attacks—like Advanced Persistent Threats, or Multi-Layer Attacks— that take a long time to defend against, or even detect. Ransomware immediately shouts “I’m an attack and I’m right here!” And then gives you 24-48 hours to either pay the ransom or suffer the loss.
Sophisticated New Attack Tools
While some of the early ransomware tools extorted individuals, these new tools are targeting businesses, hoping for a greater financial gain. New variants such as Locky, Petya, Cerber and Samas have posed operational and financial challenges to numerous businesses already. They encrypt all files on a certain server / workstation and can be decrypted and restored only if the ransom is paid to the attacker.
- Locky propagates through spam emails with infected files, and changes all file extensions to .locky.
- Samas exploits webserver’s vulnerabilities to then spread inside the network
- Petya propagates via phishing and introduces a new method of overriding hard drive MBR.
- Cerber masquerades itself as an Adobe Flash player update, impersonating to a Windows executable to pop up in the next reboot.
Ransomware attacks now join the ranks of corporate cyber ransom with other techniques like Ransom-DoS, which began in 2015. Companies are threatened with Denial-of-Service attack unless paying the ransom (read how Swiss email provider Protonmail overcame a sophisticated DDoS ransom attack). These multi-vector attacks involved over 100 Gbps volume of traffic combined with application layer attacks. The attacks also included multiple encrypted attack vectors including SSL SYN flood attacks that required advanced behavioral analysis to identify malicious traffic and maintain legitimate encrypted traffic flows.
The Armada modus operandi was quickly replicated by a couple of other groups, such as RedDoor in Germany and EzBTC_Squad. As the name of the latter suggest – they realized that Ransom attacks are profitable.
[You might also like: Ransom, Ransom Everywhere]
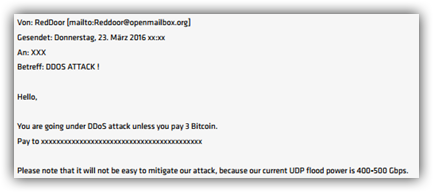
Here is an email sent by Reddoor to their victims:
All types are run in a semi manual way – meaning the hackers have to be actively engaged throughout the operation – beginning with social engineering (in Germany they targeted HR departments with infected CV’s and links. In other cases they specifically targeted corporate executives), and later once penetrated they use domain credentials, scan results and psexec.
This indicates a shift in skillset and a shift in ransomware, and provokes a real concern around the future of ransomware as it grows in sophistication, automation, and moves on to take on mobile devices too. What’s more, now just like there are DDoS for hire programs, there are also Ransom-for-hire services available in the darkweb.

Ransomware is an easy way to make quick money. It can simply shutdown a business – it threatens network availability, corporate reputation, company operations and it is very costly to fight and to remediate. Once it has penetrated the company’s network, it can easily spread among multiple servers and workstations, and company productivity will crawl. Moreover – think of the US hospitals for example – what happens if they lose crucial private patient information? That raises the question of whether HIPAA addresses recent ransomware breaches.
Ransomeware forces companies to pay a lot of money (or Bitcoins) to return operations to normal. The limited time of to find and overcome its decryption key makes it almost a mission impossible. Consequently Ransomware has a high success rate, which makes it even more popular among cyber criminals. Incident response teams dealing with 3 to 4 Ransomware incidents weekly.
So what can you do?
Researcher Leo Stone has found some flaws in the Petya program and published a decoding tool.
Radware has compiled a list of tips on how to protect yourself against ransomware attacks, which you can download here.
