Ransom, Ransom Everywhere
DDoS for Ransom is a growing concern. In the past year, we have witnessed an exponential increase in the number of ransom threats companies have received from hackers. A few groups emerged at the forefront of this trend: DD4BC, Armada Collective, and allegedly Lizard Squad.
Back in November 2015 Radware got up close and personal with DDoS extortionist Armada Collective when we helped mitigate an attack against ProtonMail. The Armada Collective threatens companies with a Denial of Service attack if they do not pay their ransom in Bitcoin within a certain time frame. Along with the note, Armada Collective launches sample attacks against their victim’s network in demonstration of their power.
After ProtonMail received their ransom letter they were hit with one of Europe’s largest distributed denial of service attacks. The Armada Collective’s attacks were gradual and methodical, thus achieving a higher success rate than most. During the first stage of the attack we saw peaks greater than 50gbps and close to a dozen different vectors of attack.
Since then we have been following a number of DDoS for ransom groups and their activities in Switzerland and throughout the world. These groups have been mainly targeting the financial, e-commerce and the hosting industry. Some have even tried to ransom government entities. They typically target any company or organization that has a large, user-dependent base. Over the past few weeks we have seen an exponential increase in DDoS for ransom threats. Ransom in general is becoming a very popular vector that hackers have been exploring and the results have produced large financial gains for some groups.
[You might also like: A View From the Corner Offices: New Research on C-Suite Security Mindset ]
In January, Dark Reading reported the arrest of key members of the Armada Collective. Since then, there appeared to be a change in the Armada Collective modus operandi. We were no longer seeing massive attacks following the ransom notes like some of our other clients.
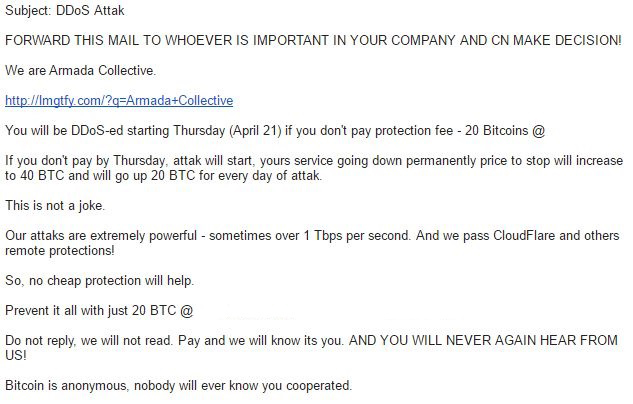
Fake Ransom Note:
Real Ransom Note:
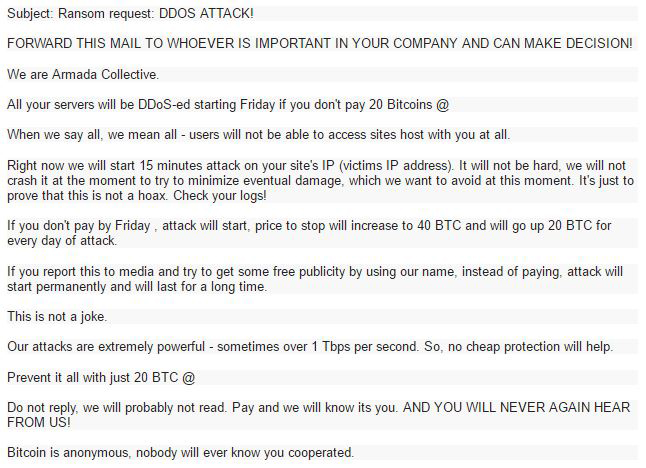
After comparing several letters and patterns behind this group, we determined that there was another hacking group now imitating the Armada Collective and sending out ransom threats similar to those behind the real group, while the major groups continued to operate. On April 27th our ERT division issued an alert to warn companies about the new trend we are seeing. The main delivery method via email had not changed but some of the context in the letters did. The new group was requesting different amounts of money and was not presenting their victims with a sample attack. In some cases, the BTC address was the same, making it almost impossible for the attackers to determine who has paid. This new group never intended to carry through on their threats. They were just spamming out ransom letters in the hopes that someone would pay fearing the known name, Armada Collective.
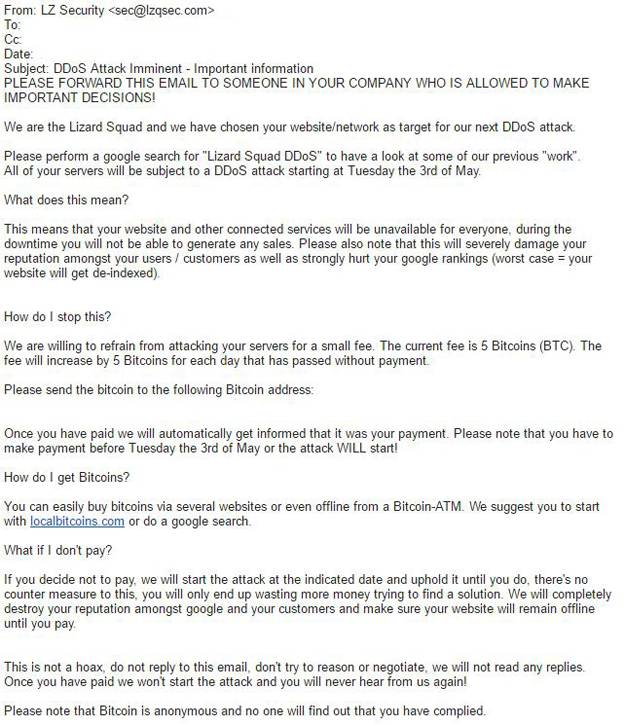
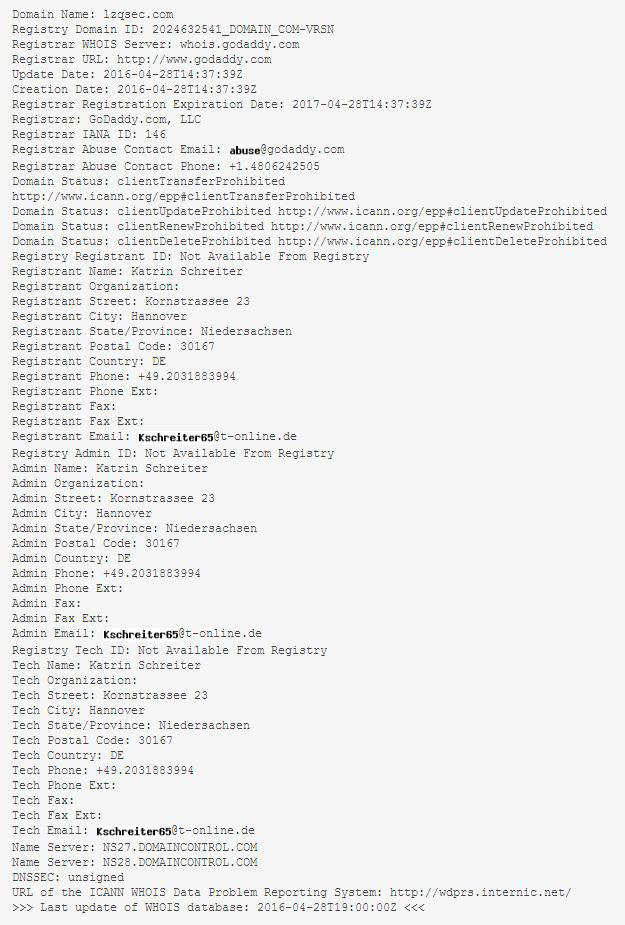
On April 28th, the day after we issued our alert, the fake Armada Collective began sending out ransom letters again but this time claiming that they were the notorious DDoS group, Lizard Squad. It was quickly determined by our ERT team that these letters were indeed bogus and came from the fake Armada Collective, like we had previously alerted. These new ransom letters came from the domain lzqsec[.]com, a domain that was created on the same day we began seeing ransom letters from this group. This time the attackers asked for 5 BTC to prevent the attack and the ransom would increase by 5 BTC for each day that passes without payment. Through different channels we were able to identify 15 separate companies that had received this ransom note with a deadline of May 3rd. Even if these threats are real, there is no way a single DDoS extortionist group could possibly target them all in one day.
We believe that the recent attention from Radware highlighting this trend may aggravate those behind this fake campaign. After being called out as a fake group, we saw them quickly try to change their name. This new attention might provoke the group into carrying out future attacks. As many of the Lizard Squad members were also arrested last summer, it is highly unlikely that they are behind these threats. Currently the group maintains a stresser service called Shenron. There is no need for them to go into the ransom business when the ransom business could easily utilize their services.
[You might also like: Ransomware Takes Center Stage as a Major Corporate Cyber Security Risk]
Ransom equals big money. DDoS for ransom groups are requesting anywhere between $2,000 – $10,000 dollars on average and the penalty for a missed payment is much larger. It’s like the saying goes, defenders have to be right 100% of the time, while attackers only have to be right once. Attackers know they can spam out hundreds of ransom letters with no intention of launching a Denial of Service attack while still get someone to pay. Technically, they only need one victim to pay to make the whole operation worthwhile. In this case with the recent Lizard Squad ransom note, if one person would have paid they would have made $2000 for the day.
Ultimately it’s hard to determine if a ransom note is real or fake. These fake DDoS for Ransom groups can change their course of action very quickly. It wouldn’t take much for them to actually start carrying out the actions behind their threats. The entry level keeps lowering, allowing novice attackers the ability to conduct much larger and more sophisticated attacks with ease. For $19.99 a month an attacker can run attacks for 30 days, 1,200 seconds at a time, and utilizing multiple vectors of attack. There are also groups out there using Booters and Stresser services to run these DDoS campaigns. As I like to say, pay my ransom before my 1,200 second attack time expires.

