Radware Mitigates 1.1Tbps DDoS Attack
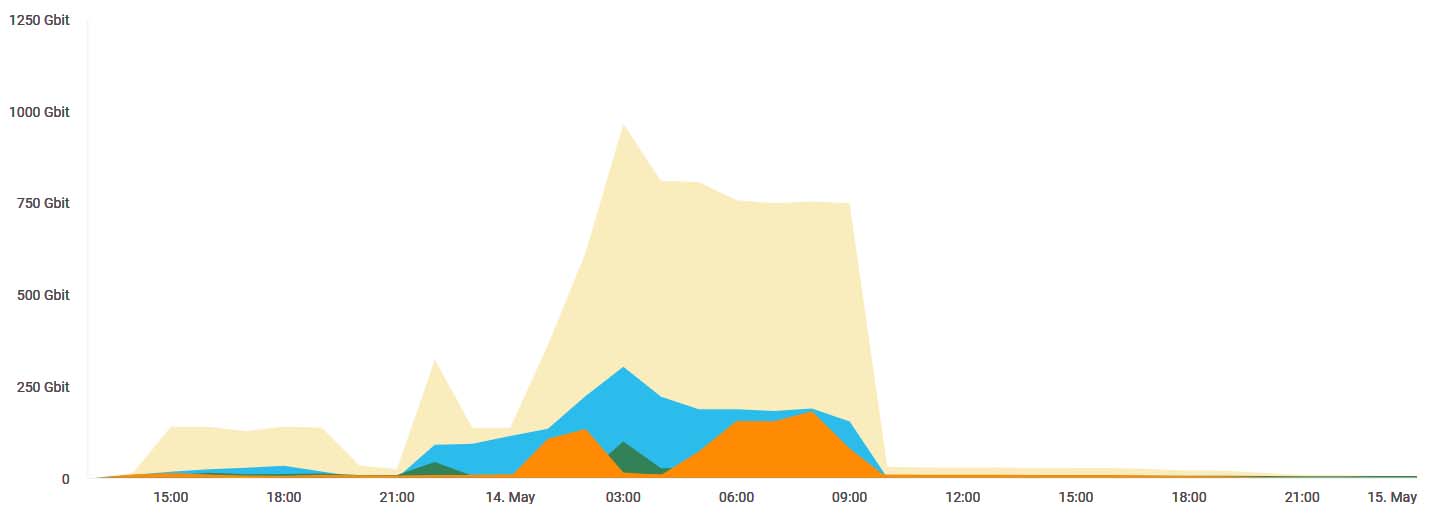
As more businesses migrate critical resources and applications to the public cloud, attackers are adapting their tactics and techniques to match the scale of public cloud providers. Last week, this trend played out as reality for one of the world’s largest service providers when it was hit by a 1.1 Tbps DDoS attack (Figure 1) that lasted approximately 36 hours. Here’s how this U.S. provider’s story unfolded.
The First Wave
The clock started ticking when this U.S. service provider noticed a service impact. At first, the service provider, which serves millions of businesses worldwide, intended to mitigate the attack using its on-premise solution as it usually does. However, a decision was quickly made to route all traffic through Radware’s Cloud DDoS Protection Service when the high-volume, multi-vector attack was too complex to handle locally.
Within a few minutes after the first call to Radware’s Emergency Response Team (ERT) hotline, the service provider’s assets were onboarded to Radware Cloud DDoS Protection Service and mitigation started.
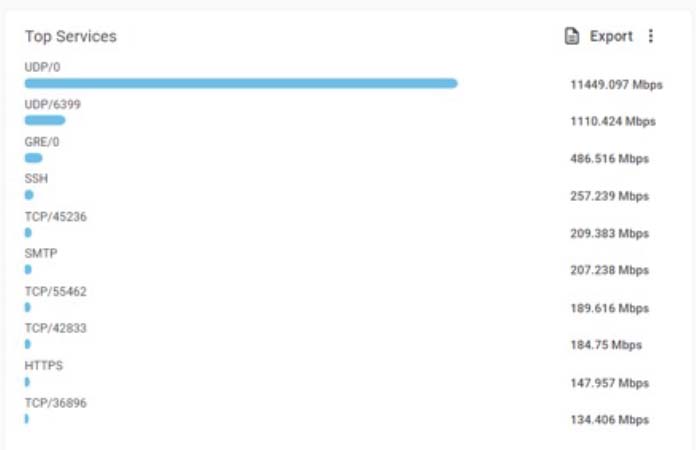
During the first five hours of the attack, traffic peaked at 150 Gbps. The top attack vectors included UDP flood, UDP fragmentation flood, fragmented ACK and PSH flood, and NTP reflection (Figure 2). With UDP flood attacks, the attacker intends to saturate the victim’s internet pipes by sending large UDP packets to a single destination or to a random port. With fragmented ACK and PSH flood attacks, on the other hand, the attacker uses very small byte packets to hog the target network’s bandwidth using only a moderate packet rate. Radware’s ERT security experts worked in collaboration with the new customer to understand normal traffic patterns and immediately applied the relevant mitigation to fully block the first wave of the attack.
[You may also like: Top Things to Look for in DDoS Protection]
The Second Wave
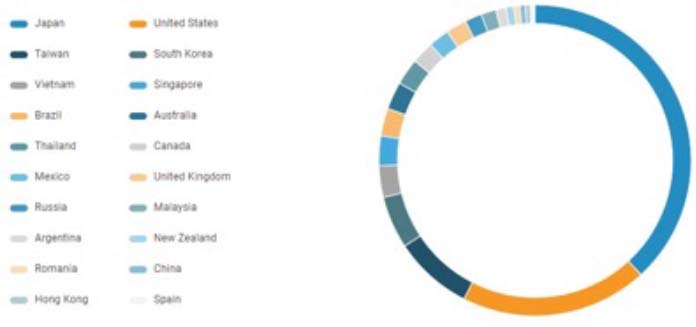
Six hours into the incident, the second wave of the attack began, with traffic peaking at over 300 Gbps. Based on evidence gathered primarily from indicators of compromise, the attack traffic appeared to have originated primarily from Japan, the United States, Taiwan, and South Korea (Figure 3).
At this point, the unrelenting attack continued. Trying to disrupt service to the provider, approximately 150Gbps of traffic lasted for an additional three hours, before peaking at 1.1 Tbps.
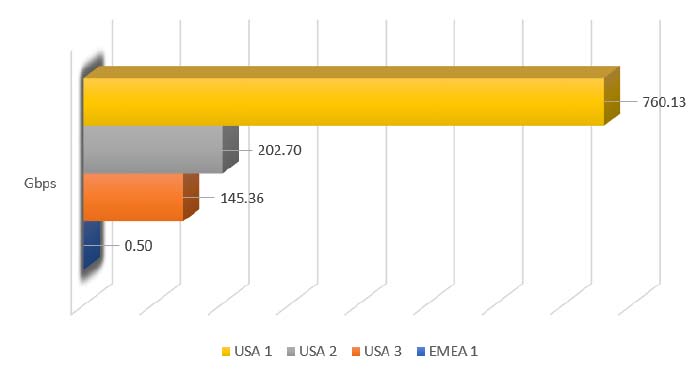
The barrage of attack traffic was fully mitigated leveraging the capacity of only four of the scrubbing centers in Radware’s global network. The scrubbing centers were located in the United States and EMEA (Figure 4).
Post Peak
Post peak, approximately 800 Gbps of attack traffic continued for more than nine hours until the attacker’s resources were exhausted by Radware’s Cloud DDoS Protection mitigation and ERT experts.
As of the time of this blog, no hacktivist organization has assumed responsibility for the attack.
Is this just the beginning?
It is impossible to ignore the wave of hyper-volumetric DDoS attacks that have been recorded in 2022. While 2021 saw only a few 1Tbps attacks, attacks of 1Tbps and more are becoming a new reality this year.
As bandwidths and resources increase for legitimate businesses, they also increase for threat actors. It is only fair to assume that bad actors can scale as fast and high as their targets. Organizations need to be aware that DDoS attacks are a part of their threat landscape, irrespective of geography or industry.
Radware’s Cloud DDoS Protection Services protect organizations of all sizes from a wide variety from sectors, ranging from education, e-commerce, retail, and global financial services to worldwide governments, and leading service providers and carriers. It is safe to say that no organization, regardless of what they do or where they are located, are immune from attack.



