Climbing the security and personal mountain in 2016
For my last blog in 2015 I’d like to address a very personal topic that has a lot in common with IT Security. A passion of mine in addition to IT Security (and, of course, supporting our customers) is to climb mountains. What is the link between this and IT Security? More than you might think.
When you climb a mountain during winter, at high elevations, or when you ski in deep snow (like a helicopter skiing tour) one of the most dangerous risks is to get hit by an avalanche. For all the “flat country” folks, an avalanche is the rapid flow of snow down a sloping surface.
 Avalanches usually accelerate rapidly and grow in mass and volume as they entrain more snow. If the avalanche moves fast enough some of the snow may mix with the air forming a powder snow avalanche. Although primarily composed of flowing snow and air, large avalanches can also entrain ice, rocks, trees, and other material in its path. If a person is trapped by an avalanche, timing is everything. The faster you find a victim, the better chance there is for survival.
Avalanches usually accelerate rapidly and grow in mass and volume as they entrain more snow. If the avalanche moves fast enough some of the snow may mix with the air forming a powder snow avalanche. Although primarily composed of flowing snow and air, large avalanches can also entrain ice, rocks, trees, and other material in its path. If a person is trapped by an avalanche, timing is everything. The faster you find a victim, the better chance there is for survival.
Avalanches are not rare or random and they are endemic to any mountain range that accumulates a standing snowpack. Due to this, many preventative measures are employed in areas where avalanches pose a significant threat to people – areas like ski resorts, mountain towns, roads, and railways.
There are several ways to prevent avalanches and lessen their power and destruction. These active preventative measures reduce the likelihood and size of avalanches by disrupting the structure of the snowpack, while passive measures reinforce and stabilize the snowpack.
The Virtual Avalanche

In an IT infrastructure, a similar risk is a volumetric DDoS attack. These attacks can create severe damage and service outages. They are like virtual avalanches for your infrastructure.
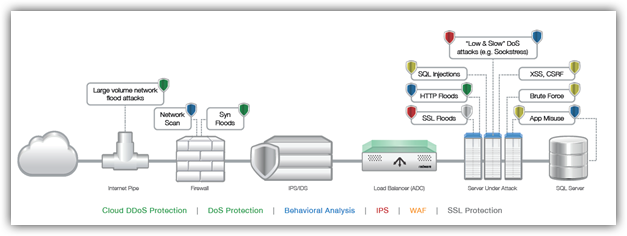
DDoS attacks that target network resources attempt to consume all of a victim’s network bandwidth by using a large volume of illegitimate traffic to saturate the company’s Internet pipe. These attacks, called network floods, are simple yet effective. In a typical flooding attack, the offense is distributed among an army of thousands of volunteered or compromised computers—a botnet—that sends a huge amount of junk traffic to the targeted site, overwhelming its network and the devices providing a specific service on this network.
Volumetric flood attacks are detected by an on-premise DoS/ DDoS protection device located at the perimeter. Once detected, mitigation starts immediately. However, attack volume threatens to saturate the Internet pipe. Soon, the pipe has been saturated and the organization is losing business, because the services are not available anymore.
To effectively mitigate all types of DDoS attacks, multiple protection tools are needed.
- Cloud DoS protection to mitigate volumetric attacks that threaten to saturate the Internet pipe.
- DoS protection to detect and mitigate all types of network DDoS attacks.
- Behavioral Analysis to protect against application DDoS and misuse attacks. Those attacks are harder to detect and appear like legitimate traffic so they can go unnoticed without a behavioral analysis tool.
- Intrusion Prevention System (IPS) to block known attack tools and the low and slow attacks.
- SSL protection to protect against encrypted flood attacks.
- Web Application Firewall (WAF) to prevent web application vulnerability exploitations.
The Human Factor
When you climb a mountain you have to do a clear and solid risk assessment before you start. What are the weather conditions? Am I in good enough shape for this climb? Am I protected enough?
These questions tie to human factors that should be considered in mountain climbing and in IT Security – the tendency to underestimate risk and overestimate personal skills and capabilities.
Underestimating Risk
When you go climbing conditions can change rapidly, so underestimating risk can be a serious issue and this can leave you unprepared. For DDoS attacks, there is similar notion I still see with many IT managers and business owners – the assumption that attacks will not happen to them. But what I know and see in everyday business, is that it is not a question of IF a company will become a victim of a cyber-attack, but a question of WHEN.
In the 2015 Application and Network Security Report, there’s evidence that cyber-threats are growing and expanding to new targets. The technical “bag of tricks” is bigger than ever and even organizations with by-the-book security programs can be caught off guard.
Overestimating Capability
Have a look at the picture below. What do you think will be required to ride down this slope?
More than what you may think. Beyond above average skills, a rider would need specialized equipment, transportation and a partner for safety.
Another detrimental requirement is that the climber clearly understands their own capabilities and skills. If they don’t, climbers can risk their health or life and could also put their team into a dangerous situation because they take care and cover you.

If you’re ever able to make such a ride, it will be a “once in a lifetime” experience you will never forget!
An average skier or snowboarder will have difficulties on a trail like this and an average network manager will likely have difficulty fighting off a DDoS attack.
Often the skill set from a sophisticated cyber-attacker may outreach the knowledge and experience of a regular IT team. Does your team have the skills required? What would happen if they lose this battle? How crucial is your infrastructure and what is the maximum damage you can accept?
It is crucial to pick the right partner and the best team to fight against today’s cyber-attacks. An educated, skillful team will make sure your services and applications are protected and stay online, all the time.

The Radware ERT
Therefore it is crucial to pick the right partner and the best team which is educated and has the required skill set to fight against todays cyber-attacks. This will make sure your services and application will be protected and stay online, all the time.
There are many more commonalities between those two fields, but honestly, to touch all of them would end up in a small book and not blast this blog. I am happy to discuss both areas when we meet next time at one of our shows or as part of a personal meeting.
As this is my final blog for 2015, I wish all our Radware customers, partners and of course all I know personally a successful 2016 and hope you will reach your personal and security mountain.

