ALERT: OpKillingBay Threats on the Rise
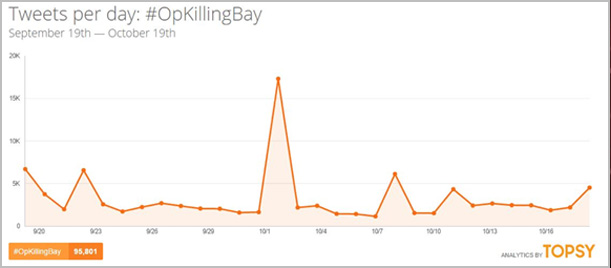
OpKillingBay is a yearly hacktivism operation by Anonymous, activists and other organizations in response to the hunting of whales and dolphins in Japan and Denmark. This year’s denial-of-service (DoS) attacks began in early September with an uptick in attacks in October following a TweetStorm earlier in the month.
This year OpKillingBay featured a two front campaign: one for Japan and the hunting of dolphins and the other for Denmark and the hunting of whales. Each campaign featured their own website and information regarding each operation. The Denmark operations are distinguished from the Japanese operations with the hashtag #OpKillingBay #EU.

“Whaling was outlawed in 1986 by the International Whaling Commission, but dolphin hunts remain legal, The Must be change #OpKillingBay”
Anonymous organizers prepare content for TweetStorms, videos, target lists and websites. The OpKillingBay website for Japan this year featured pre-scripted tweets that included @mentions, hashtags and images for each tweet. They also provided pre-scripted tweets for the TweetStorm in English, Japanese, Dutch, French, German, and Spanish. In addition, they provided scripted tweets designed to call out sponsors of the upcoming Olympics in Japan.
Operation Websites:
- EU https://sites.google.com/site/opkillingbayeu/tweets
- Japan https://sites.google.com/site/opkillingbay2/
Each operation also provided their own target list for other hacktivists to attack.
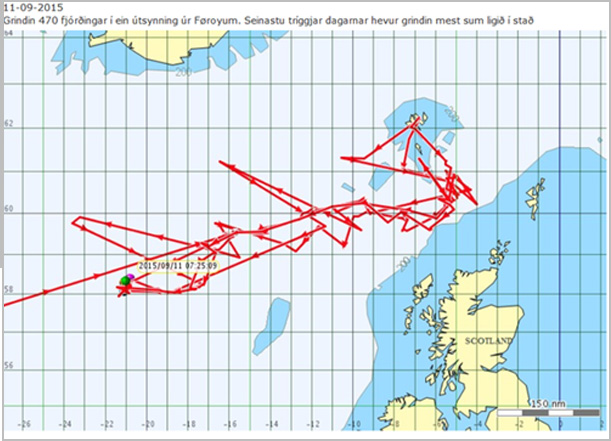
Savn.fo was targeted after it was discovered to be used to track whales
This year the attackers behind OpKillingBay targeted a wide variety of industries on both fronts of the operation.
Industries:
[one_half]
- Transportation
- Retail
- Banks
- Government
[/one_half]
[one_half_last]
- Media
- Tourism
- Worker Union’s
[/one_half_last]
A single hacker that goes by the handle RektFaggot has attacked over 28 targets from Denmark to Japan since the beginning of September. Rekt has been one of the main hacktivist for OpKillingBay. The hacker has provided target lists, scan reports, data dumps and directly attacked victims. In addition to OpKillingBay, Rekt has also engaged in OpSeaWorld, OpWhales and OpFunKill.
OpKillingBay: 28+ Sites attacked by Rekt since the beginning of September
[one_half]
- unyuroren.or.jp
- Town.koya.wakayama.jp
- town.kudoyama.wakayama.jp
- town.taiji.wakayama.jp
- town.taiji.lg.jp
- cypress.ne.jp
- whaling.jp
- plala.or.jp
- japanpost.jp
- jnto.go.jp
- narita-airport.jp
- centrair.jp
- the-japan-news.com
- ascii.jp
[/one_half]
[one_half_last]
- smyrilline.dk
- savn.fo
- lindin.fo
- faroeislands.fo
- chw.jp
- city.iwade.lg.jp
- drekin.fo
- elektron.fo
- borg.fo
- shimoda-aquarium.com
- aburatsubo.co.jp
- marine-world.co.jp
- ven.fo
- sif.fo
[/one_half_last]
OpSeaWorld: 11+ Sites attacked by Rekt since the beginning of September
[one_half]
- Sochiaquarium.ru
- Marineland.fr
- Georgiaaquarium.org
- Zoo.pt
- Tiergarten.nuernberg.de
- Gulfarium.com
[/one_half]
[one_half_last]
- Bodrumdolphinpark.com
- Dolphin-academy.com
- Dlfinarium.nl
- Curacaodolphntheraphy.com
- Mundomar.es
[/one_half_last]
OpWhales: 1 Site attacked by Rekt since the beginning of September
- Iceland.is
OpFunKill: 2 Sites attacked by Rekt since the beginning of September
- Denmark.dk
- Gordonramsay.com
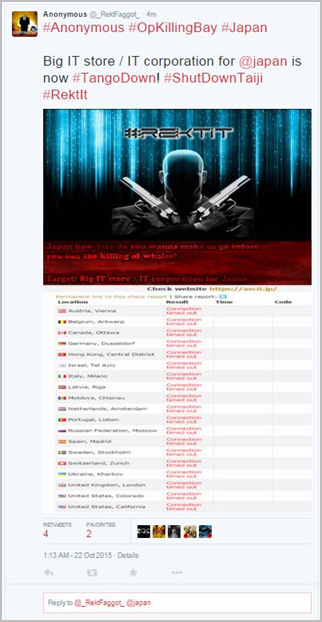
In this series of attacks, we have seen SQL injections, data dumps and service outages cause by denial-of-service attacks from ongoing campaigns by Anonymous. OpKillingBay has targeted a number of industries directly and indirectly related to the hunting of dolphins and whales. Attacks like these are hard to avoid. At the core of the problem are ideological differences. The victims of these attacks are conducting business within the letter of the law. The actions of the groups behind OpKillingBay are driven from an emotional and social justice perspective. These two sides may never see eye to eye and this could result in a persistent state of attacks.
These attacks aim to cause service outages due to vulnerabilities in server applications or a large amount of traffic aimed at a weak network. Radware offers a full range of solutions to help your network properly mitigate attacks like the ones seen during OpKillingBay. Our DefensePro system can help provide your network with real-time behavioral based attack mitigation. Our Attack Mitigation Services (AMS) can also aid in detection and mitigation with cloud based volumetric attack scrubbing.
In addition to Radware products, it is recommended that you review your network once a year during the month of August. These attacks happen yearly before the start of the fishing season in September. Maintaining and inspecting your network is necessary if you are facing yearly attacks from hacktivists like those involved with OpKillingBay.
For more Information about this alert visit: http://global.radware.com/LP=242
Reports
- “Server high-load” http://www.plala.or.jp/support/network/kosyo/tokyo/?entry_id=172221
- “DDoS” http://the-japan-news.com/news/article/0002482799
- “Increase in server load.” http://www.jnto.go.jp/jpn/news/info/20151013.pdf
Sources
- Scripted tweets https://sites.google.com/site/opkillingbay2/olympic-sponsors-tweets
- OpKillingBay attacks
- https://twitter.com/_RektFaggot_/status/656119962688462848
- unyuroren.or.jp
- https://twitter.com/_RektFaggot_/status/654717192290758658
- Town.koya.wakayama.jp
- town.kudoyama.wakayama.jp
- https://twitter.com/_RektFaggot_/status/656538715846787072
- Town.taiji.wakayama.jp
- Town.taiji.lg.jp
- Cypress.ne.jp
- Whaling.jp
- https://twitter.com/_RektFaggot_/status/654368177913204736
- Plala.or.jp
- https://twitter.com/_RektFaggot_/status/653254957395783680
- Japanpost.jp
- https://twitter.com/_RektFaggot_/status/652855406587441152
- Jnto.go.jp
- https://twitter.com/_RektFaggot_/status/652545257314324480
- Narita-airport.jp
- Centrair.jp
- https://twitter.com/_RektFaggot_/status/652329142961242112
- The-japan-news.com
- https://twitter.com/_RektFaggot_/status/656881010727108608
- Ascii.jp
- https://twitter.com/_RektFaggot_/status/647744781611855872
- Smyrilline.dk
- https://twitter.com/_RektFaggot_/status/642830002279555072
- Savn.fo
- https://twitter.com/_RektFaggot_/status/641265260071141376
- Lindin.fo
- Faroeislands.fo
- Chw.jp
- city.iwade.lg.jp
- https://twitter.com/_RektFaggot_/status/640608852900249600
- Drekin.fo
- Elektron.fo
- Borg.fo
- https://twitter.com/_RektFaggot_/status/639509436495757313
- shimoda-aquarium.com/
- aburatsubo.co.jp/
- marine-world.co.jp/
- https://twitter.com/_RektFaggot_/status/639140679717912576
- ven.fo/
- sif.fo
- https://twitter.com/_RektFaggot_/status/656119962688462848
- OpSeaWorld
- https://twitter.com/_RektFaggot_/status/655503384691261441
- Sochiaquarium.ru
- https://twitter.com/_RektFaggot_/status/654278296222494720
- Marineland.fr
- https://twitter.com/_RektFaggot_/status/643887925453803520
- Georgiaaquarium.org
- Zoo.pt
- Tiergarten.nuernberg.de
- Gulfarium.com
- https://twitter.com/_RektFaggot_/status/643872281807187968
- Bodrumdolphinpark.com
- https://twitter.com/_RektFaggot_/status/641710014164541440
- Dolphin-academy.com
- Dlfinarium.nl
- Curacaodolphntheraphy.com
- Mundomar.es
- https://twitter.com/_RektFaggot_/status/655503384691261441
- OpWhales
- OpFunKill
- https://twitter.com/_RektFaggot_/status/654034206494957568
- Denmark.dk
- https://twitter.com/_RektFaggot_/status/643053070948147200
- Gordonramsay.com
- https://twitter.com/_RektFaggot_/status/654034206494957568
To learn more about how you can protect your organization from attack, please download our DDoS Handbook.
