The Danger of API Security Overconfidence: Four Takeaways from Radware’s 2022 State of API Security Survey
A short list of the companies that have suffered recent API-related breaches are a who’s-who of the global technology brain trust: Microsoft, Venmo, Equifax, Instagram, Facebook, Amazon, PayPal, and many others.
If even these tech-savvy organizations are subject to cyberattack, the reality couldn’t be more clear: there is a pervasive false sense of security that companies are adequately protected from cyberattack, and this disconnect results from significant gaps in securing APIs that are unknown or undocumented, and therefore unsecured.
APIs are critical—and vulnerable
APIs are a fundamental component to most of the current technologies and securing them must be a priority for every organization. According to our recent 2022 State of API Security Survey, conducted with Enterprise Management Associates, 92% of organizations surveyed significantly or somewhat increased their API usage in the last year (see Figure 1) with 59% already running most of their applications in the cloud.
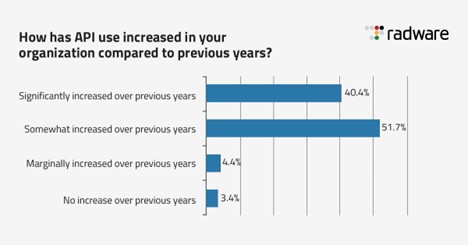
Yet there is over-confidence when it comes to API protection. This was demonstrated across the results of the survey.
Here are four key takeaways from the survey:
The threat of undocumented APIs is real and underestimated. While 92% of those surveyed believe they have adequate protection for their APIs and 70% believe they have visibility into applications that are processing sensitive data, 62% admit a third or more of APIs are undocumented. Undocumented APIs leave organizations vulnerable to database exposures, data breaches, and scraping attacks.
[You may also like: How to Keep APIs Secure in an Interconnected World]
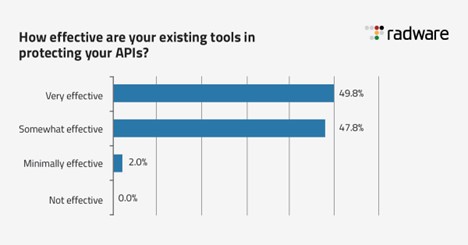
API attacks are flying under the radar. Half of companies surveyed viewed their existing tools as only somewhat or minimally effective at protecting their APIs (see Figure 2), with 7% reporting that the solutions they have in place did not identify any attacks at all. The inability of the existing tools to adequately protect APIs from common threats further adds to the false security narrative.
Open source contributes to the security myth. Sixty-five percent (65%) of respondents believe that open-source code is more secure than proprietary code. In addition, nearly 74% believe that container-based deployment and microservice architecture are more secure than monolithic architecture and deployment by default.
The belief that open source is more secure by design could explain why some organizations are lax when it comes to patch management. Yet, as we have seen with Log4j and Heartbleed, open source can have the same security flaws as proprietary code. Believing that open source is inherently more secure by default only further contributes to the false narrative that leaves organizations vulnerable to cyber-attacks.
Bot attacks remain a threat along with misperceptions about API protection.
The survey data indicates that API protection is not keeping up with API usage. Nearly one third of companies (32%) surveyed stated that automated bot attacks are one of most common threats to APIs. In terms of detecting an API attack, 29% say they rely on alerts from an API gateway and 21% rely on web application firewalls (WAF). These organizations are basing their API security approach on a false belief — namely that API gateways and traditional WAFs offer sufficient protection — which leaves their APIs vulnerable and exposed to common threats, like bot attacks. A comprehensive API protection solution, that includes bot protection, will address these threats, but very few respondents indicated that they had solutions that actually did, or even had the capability to do so.
[You may also like: 4 Assumptions Preventing Effective API Protection]
A comprehensive API protection solution is a must.
Protecting APIs is not a simple task – it requires an in-depth understanding of a multitude of environments and platforms. An effective API security solution will have most of the following capabilities:
- Integrates well with existing security and visibility tools in the environment.
- Leverages advanced machine-learning algorithms to detect emerging threats and automatically creates and optimizes API security policies.
- Enables accurate and automated API discovery, protection, and security policy generation without requiring application or security expertise
- Provides comprehensive API protection of all parts of the API and across a broad range of API threats, including access violations, data leakage, denial of service, automated threats (bots), and embedded attacks.
- Protects APIs against automated, bot-based threats.
- Supports both positive and negative security models while enabling continuous and automatic security policy optimization and adjustments to correct and eliminate false positive events.
It is also critical to find solutions and tools that allow organizations to easily protect their APIs regardless of their location. Any tool that requires an entire security team to administer is not going to be a viable tool to protect APIs in most organizations. A reoccurring theme in the security space is the lack of security talent. Even the most experienced security administrator may not have the development skills necessary to architect and deploy a best-in-class security strategy for protecting APIs and application workloads.
API security may not be making news headlines like ransomware and DDoS attacks — but it is a trend that is not going away any time soon.
To download a full copy of the survey, click here.



