Turkey DNS Servers Under Attack
Since Monday December 14th, Turkey’s DNS servers, ns1.nic.tr – ns5.nic.tr, have been the target of a persistent denial of service attack. This 40Gbps amplification attack targeted all 5 nic.tr servers and saw peaks close to 200 Gbps. The attack left more than 400,000 websites down in Turkey and DNS servers unable to respond to queries.
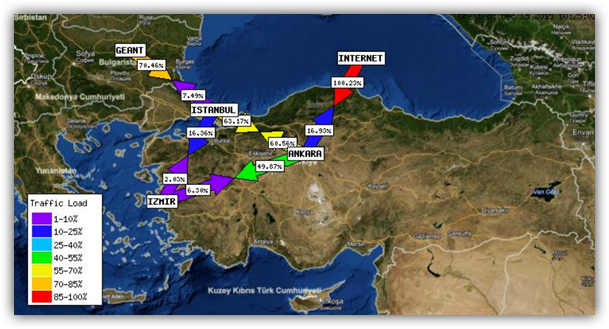
https://stat.ulakbim.gov.tr/ulaknet/
All traffic to Turkey was eventually cut off in an attempt to mitigate the attack. As of December 20th the DNS servers were still being targeted. The attacks are coming from spoofed addresses, masking the origin of the attack.
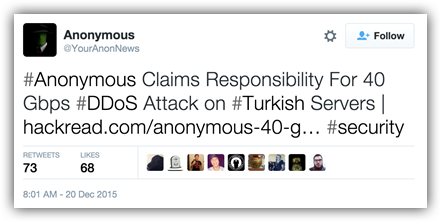
Recently Anonymous has taken credit for the attacks under the ongoing operation, OpISIS. In a newly release video by Anonymous they claim they are targeting Turkey due to Erdogan’s support of ISIS. They go on to claim that Turkey is buying oil from ISIS and vows to keep attacking until they stop supporting them.
Video by Anonymous – Message to Turkey: https://youtu.be/0m9lzxXIDBU
Please read Radware’s Emergency Response Team alert for further details.
