Visibility into Peacetime Traffic. Is it Too Much to Expect From Your DDoS Protection Provider?
Today, everyone has at least one insurance policy. It could be a healthcare, automobile, or life insurance policy. We invest heavily in these policies and have high expectations for a return on our investment when the unforeseen happens and we need the protections they provide. But most of us don’t expect anything from our insurance companies during “peacetime” — a period of time when there are no incidents or accidents.
Making peacetime part of the service policy
While a DDoS protection solution resembles an insurance policy in many ways, it should perform even better. Organizations should expect a high degree of service and network visibility from their security providers even during peacetime.
However, like insurance companies, most cyber security companies don’t service their clients during peacetime. Many clients simply do not expect it from their vendors, just like we as consumers don’t expect it from our insurance companies.
At Radware, we believe that clients should expect more from their security vendors. That’s why we are committed to servicing clients when they are under attack, during peacetime — and all year round.
[You may also like: Does Your DDoS Protection Solution Defend Against the Latest Attacks?]
Proactive protection in peacetime
As part of our Cloud DDoS Protection Service, Radware is offering a new Cloud Network Analytics Service, which offers full visibility into network traffic, both during peacetime and when under attack. Network managers will now have a complete picture (see Figure 1) of non-aggregated daily traffic data, spanning 90 days.
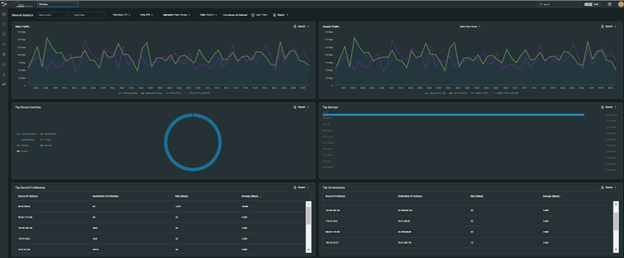
The new service provides analytics and visibility across four key areas: network traffic visibility, services in use, access privileges management, and client-server traffic.
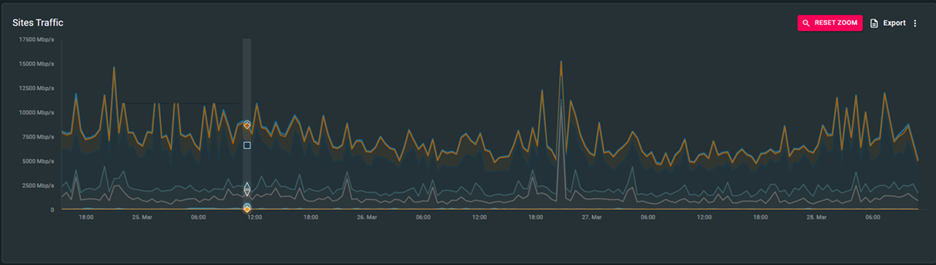
Network Traffic Visibility: Our Cloud Network Analytics Service reports on the exact amount of traffic moving across an organization’s network at any given time. Understanding network consumption enables more effective network planning and deployment to avoid scaling and sizing issues (See Figure 2). For instance, having detailed data about peacetime traffic in hand can be particularly valuable for organizations working with service providers to size the right network. Clear visibility into peacetime traffic leads to more accurate planning and pricing, and ultimately reduces the costs associated with unnecessary bandwidth.
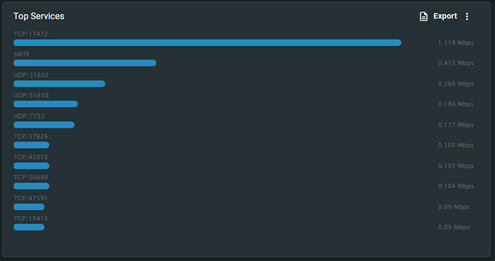
Services in Use: Our analytics service offers a detailed overview of and the ability to monitor services in use, such as HTTPS, DNS, internet browsing, VoIP, file downloading, and more. That way organizations can make sure their services are used for the right purpose (see Figure 3). For example, an unexpected and unusual spike in use is a flag that a service should be investigated.
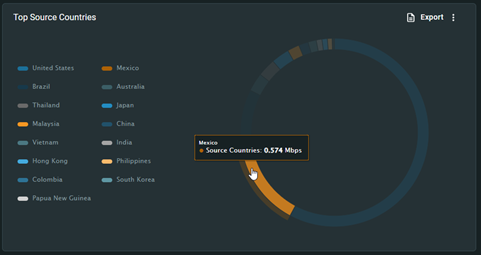
Access Privileges Management: To ensure users have proper access to the right systems, our Cloud Network Analytics Service maps users and their access privileges as well as the specific IP addresses and geographies that can access an organization’s services (see Figure 4).
Client-Server Traffic: Our new service also quantifies the amount of traffic flowing between each client to the server, monitoring conversations and making sure users aren’t abusing server conversations or resources. This type of reporting is helpful in detecting the possible abuse of credentials.
It is finally time for companies to demand a little more than the obvious from their security providers and start getting their money’s worth. Even if used in different settings and circumstances, data about peacetime traffic is just as valuable as data about attack traffic — and no one should settle for less.



